In order to fully understand a company's security risks and understand your GDPR Data Mapping requirements, we must first analyze the workflow of the sensitive data.
What is the Data Flow Analysis?
A thorough analysis of how an organization's users are utilizing their sensitive data in rest and in motion in ways that vulnerability scanning tools cannot detect. The purpose of this is to define necessary GDPR required Data Maps and understand boundaries for security responsibilities as well as confirm that data transmission is secure and protected from a compliance perspective.
What are Data Maps?
As part of GDPR compliance, organizations are required to map their data and information flows in order to assess their privacy and to form part of their registration documentation. To effectively map their data, an organization needs to understand the information data flow, and identify its key elements. Learn more about GDPR Data Maps here.
Data Flow Analysis Phases
The Data Flow Analysis phase of the risk assessment is completed in two parts:
- Data Flow Questionnaires
- Sent to all employees within the organization
- Designed to take approximately 10-15 minutes to complete by each team member
- Data Flow Interviews
- Interviews are conducted with 1-2 resources per department that store or transmit sensitive data discovered in the Questionnaire
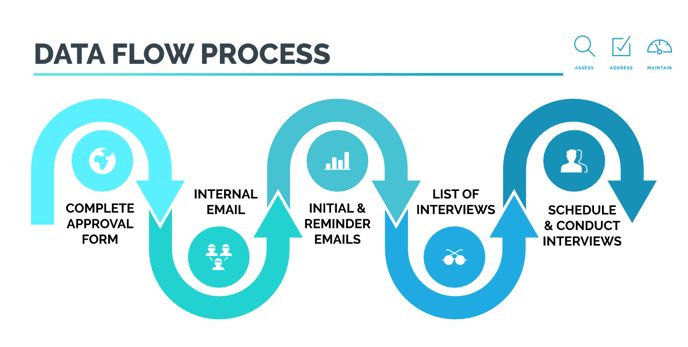
|
Client Approvals & List of Users |
|
|
| Internal Client Management Email |
|
|
| Choice Questionnaire Emails |
|
|
| List of Interviewees |
|
|
| Conduct Interviews |
|
|
| Data Review & Analysis |
|
Client On-boarding Responsibilities
- Gather a list of all users
- We prefer a spreadsheet with first name, last name, email address & department
- Please be sure to indicate any resources you feel are critical as part of this process
- Check Your Email to review and Complete the Choice CyberSecurity Data Flow Questionnaire Approval Form provided
- At the end of the questionnaire, you will be prompted to provide a list of participants and their email addresses
- Once approved, we will send another email with the Management Email Template and unique form for you to Send Management Team Email to all Questionnaire participants
- Alert Choice team when email has been sent to begin our email process approximately 2 business days after your email has been sent
Please DO NOT send the Data Flow Analysis Approval Form to your users. The approval questions at the end will confuse them and it is not designed to collect results from more than one team member.
